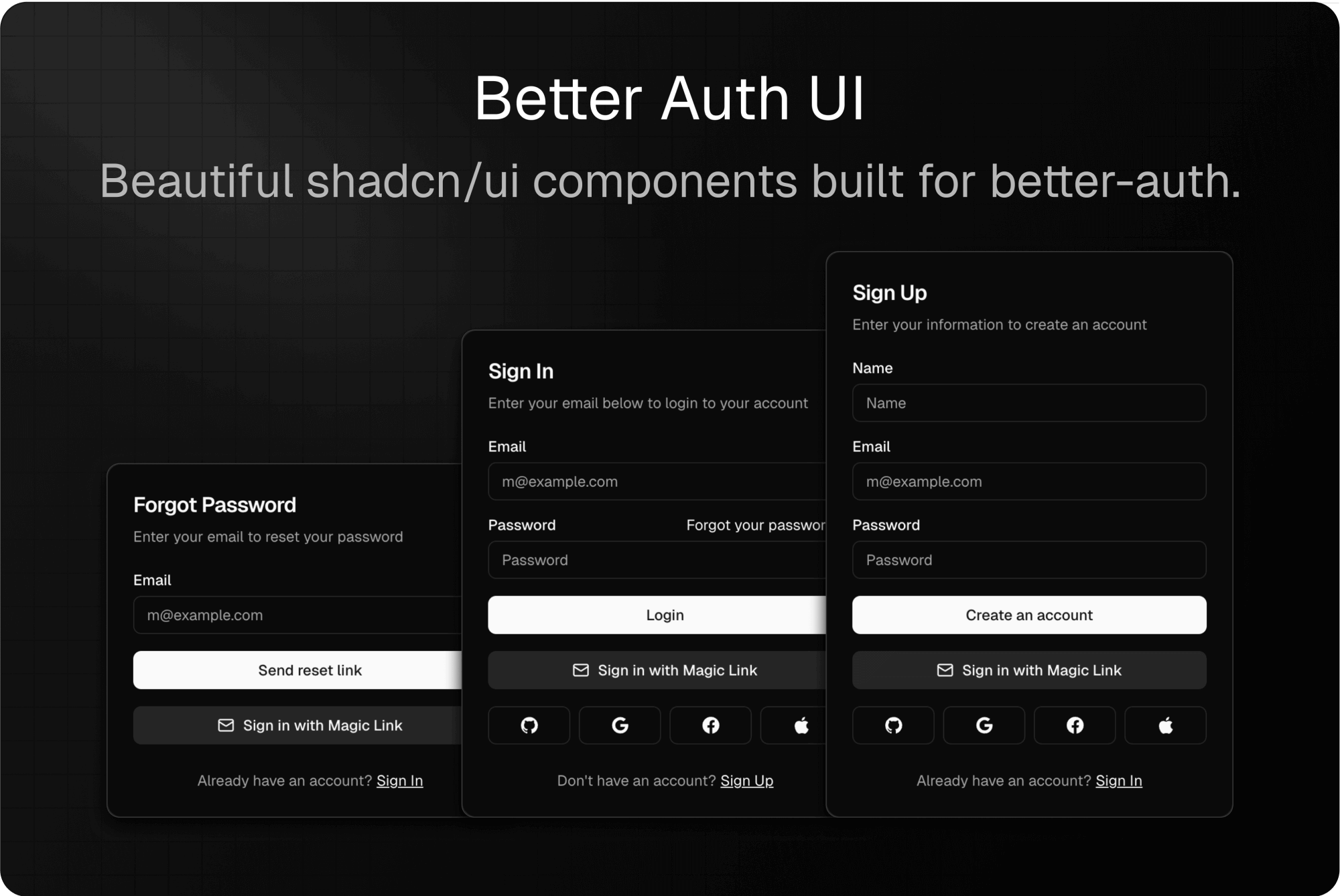
Login screens are usually where good apps go to die. You know the feeling. You find a cool new tool, click "get started," and suddenly you’re staring at a blank white box asking for a password with fourteen special characters, a blood sample, and your third grade teacher's maiden name. It’s clunky. It feels like 2005. This is exactly why the auth kit ui service has become such a massive deal for developers lately.
People don't want to "sign up." They want to use the thing.
Building an authentication flow from scratch is a nightmare. Honestly, it's one of the most thankless jobs in software engineering. If you get it right, nobody notices. If you get it wrong, your user data gets dumped on a dark web forum and your company’s reputation is toasted. The auth kit ui service approach basically says: "Stop trying to be a security expert and just use a pre-built, hardened, and actually pretty interface that works."
💡 You might also like: Why Cybertruck Pictures Still Break the Internet and What They Actually Reveal
What’s Actually Happening Under the Hood?
When we talk about an auth kit ui service, we aren't just talking about a couple of input fields for an email and password. We are talking about the entire visual and logic layer that sits between your user and their data. Think of providers like WorkOS, Clerk, or even the Frigade components. These aren't just "widgets." They are hosted or semi-hosted services that handle the messy stuff—Multi-Factor Authentication (MFA), "Magic Links," and Social Login (OAuth)—without you having to write 5,000 lines of CSS.
It’s about abstraction.
Years ago, you’d have to manually integrate the Google Sign-In API. Then you’d do Facebook. Then Apple. Then you’d realize your enterprise customers want SAML or SSO, and suddenly you’ve spent six months building a login page instead of building your actual product. An auth kit ui service handles that handoff. You drop in a snippet of code, and suddenly you have a UI that looks like it was designed by a world-class agency, but functions with the security of a bank.
The Problem With DIY Auth
Let's be real. Most "homegrown" auth UIs are ugly. They don't handle edge cases. Does your login box shake when there’s an error? Does it have a "forgot password" flow that actually works on mobile? Most don't.
Beyond the aesthetics, there's the "state" problem. Authentication is stateful. You have to track if the user is logging in, if they're pending verification, or if their session has expired. Managing that logic in your frontend code is a recipe for spaghetti. By moving this to a dedicated auth kit ui service, you’re basically outsourcing the state management. The service tells your app, "Hey, this person is legit," and your app just says, "Cool, welcome back."
Why Design Matters for Security
It sounds counterintuitive, but a better UI actually makes your app more secure. Why? Because users are lazy. If a login flow is difficult, they’ll use the same password they use for everything else. If you make it easy to use a passkey or a magic link through a clean auth kit ui service, they’ll actually use those more secure methods.
Take Passkeys, for example. Most people have no idea how to implement WebAuthn manually. It’s a massive headache. But a modern auth kit ui service usually has a toggle for it. You flip a switch, and now your users can log in with FaceID.
That’s a huge win for both UX and security.
Real World Examples: Clerk and WorkOS
If you look at how companies like Vercel or Stripe handle their user onboarding, it’s seamless. They aren't reinventing the wheel.
- Clerk: They’ve basically cornered the market on React-based auth UIs. Their components are highly "opinionated," meaning they look good out of the box and handle things like user profiles and organization switching natively.
- WorkOS: This is the "Enterprise" version. If you need to sell your app to a big company, they’re going to demand SSO. Building a UI for SAML configuration is a special kind of hell. WorkOS provides an auth kit ui service specifically for this "Admin Portal" experience.
The Myth of "Full Control"
A lot of senior devs hate the idea of using a third-party UI service. They say, "I want full control over my brand."
Sure.
But at what cost? You can spend three weeks pixel-pushing a login button, or you can use a kit that allows for "headless" UI. Many modern auth kit ui service providers now offer unstyled components. You get all the logic, all the security, and all the API hooks, but you bring your own Tailwind classes. You get the control without the liability.
It’s the best of both worlds, really.
Common Misconceptions About These Services
People think these services are just for "simple" apps. That’s just not true anymore. Even massive platforms are moving away from maintaining their own auth UIs.
- "It's too expensive." Is it? Calculate the hourly rate of two senior developers working for a month. Now compare that to a $50/month SaaS fee. The math almost always favors the service.
- "I'm locked in." This is a valid concern, but most reputable auth kit ui service providers use standard protocols like OIDC (OpenID Connect). If you want to leave, your users' data is usually exportable. You aren't "trapped" as much as you think.
- "It slows down my site." If anything, a hosted UI can be faster because it’s often served from an edge CDN closer to the user than your own backend might be.
How to Choose the Right One
Don't just grab the first one you see on GitHub. You need to look at your stack. If you’re using Next.js, Clerk is a no-brainer. If you’re building a B2B tool where people need to manage their own teams, you need something that handles "Organizations" as a first-class citizen.
Check for "Themeability." Some services are "all or nothing." You either use their purple buttons or you’re out of luck. Avoid those. Look for services that offer a "headless" mode or at least robust CSS variables.
The Role of Shadow DOM and Security
One technical detail people miss: many of these kits use the Shadow DOM. This prevents your app's global CSS from accidentally breaking the login box. It also provides a tiny bit of extra security by isolating the auth fields from malicious scripts that might be running on your main page. It’s a small detail, but it’s why a dedicated auth kit ui service is often safer than a bunch of copy-pasted code from a tutorial.
Actionable Steps for Implementation
If you’re ready to stop building login forms by hand, here is how you actually move forward without breaking your existing setup.
Audit your current friction. Open your app in an incognito window and try to sign up. Count the clicks. If it takes more than 30 seconds, you’re losing users. This is your baseline.
Start with a "Headless" trial. Don't rewrite your whole app. Pick one small flow—maybe the "Account Settings" page or the "MFA Setup"—and replace it with a component from an auth kit ui service. This lets you test the developer experience without a "big bang" migration.
Prioritize Social and Passkeys. If your chosen kit doesn't make it easy to add Google or Apple login, dump it. The whole point of using a service is to get these features for "free" (in terms of dev time).
Check the "Admin" experience. A good auth kit ui service isn't just for your end-users. It should also provide you, the developer, with a dashboard where you can actually see who is logged in, impersonate a user for support, and manually reset sessions. If the service doesn't have a solid backend dashboard, it’s only half a solution.
Stop building things that aren't your core product. Your users don't care about your custom-coded hashing algorithm or your hand-crafted CSS transitions on the "Submit" button. They care about getting into your app. Use a service, get it done in an afternoon, and go back to building the features that actually make you money.