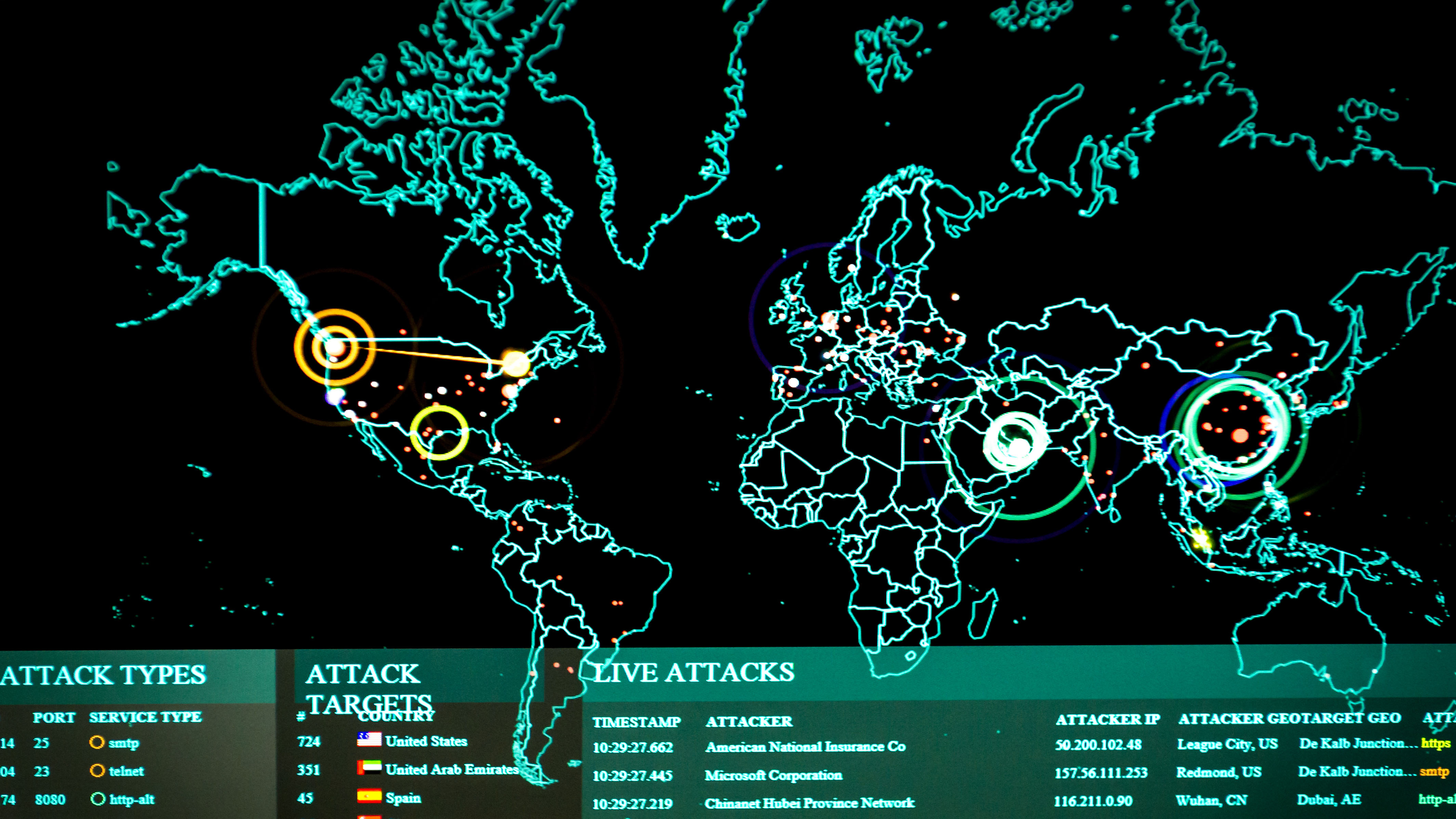
You've seen them. Those neon-streaked digital globes where glowing lines arc from one continent to another like a 1980s sci-fi movie. It looks like WarGames. It's flashy. It’s mesmerizing. But honestly? Most people looking at an internet ddos attack map aren't actually seeing what they think they are.
Distributed Denial of Service (DDoS) attacks are basically the digital equivalent of a billion people trying to walk through a single revolving door at the same time. Everything jams. The door breaks. The business inside loses money. When you watch these maps, you’re seeing that chaos in real-time. Or, at least, a very specific, filtered version of it.
Digital maps from companies like Kaspersky, Netscout, or Fortinet make for great eye candy on a SOC (Security Operations Center) monitor. They impress the boss. They look great in news reports. However, there is a massive gap between the "pew-pew" lasers on your screen and the actual packet loss happening at a data center in Virginia or Singapore.
The truth about your favorite internet ddos attack map
Here is the thing: no single map shows everything. It’s impossible. The internet is too big, too fragmented, and too private for one company to have a god-eye view of every malicious packet.
Take the NETSCOUT Cyber Threat Horizon map. It's legendary in the industry. They get their data from the ATLAS platform, which monitors a massive chunk of all internet traffic. When they show a spike in traffic hitting a specific port, it’s based on hard telemetry. But even then, it’s a sample. It’s a "best guess" based on the massive pipes they monitor.
Then you have the Kaspersky Real-time Cyberthreat Map. It’s arguably the prettiest. It spins, it glows, and it lets you zoom into specific countries to see if they are "top attacked." But wait—that map mostly shows detections from Kaspersky’s own antivirus software. If a botnet is attacking a server that doesn't use Kaspersky, it might not show up there at all.
💡 You might also like: Why the Google Python Style Guide Still Matters for Modern Devs
Why the visual data is often misleading
Most people assume the "source" country on the map is where the hacker is sitting in a dark room with a hoodie. Nope. Not even close.
DDoS attacks rely on botnets. These are armies of infected devices—your neighbor's smart fridge, an unpatched CCTV camera in Brazil, or a compromised server in a high-speed data center in Germany. When the map shows a line coming from China and hitting the US, it just means the "bots" are located there. The person pulling the strings could be sitting in a coffee shop in London using a VPN.
We also have to talk about "reflection" attacks. This is a sneaky move where attackers send small requests to legitimate servers (like DNS or NTP servers) but spoof the return address to be their victim’s IP. The legitimate server then blasts a massive response at the victim. On an internet ddos attack map, it might look like the DNS server is the attacker. It’s a hall of mirrors.
The heavy hitters of live threat tracking
If you actually want to use these tools for more than just a screensaver, you need to know who provides the most "honest" data. It’s a short list.
Cloudflare’s Radar is probably the current gold standard for transparency. Because Cloudflare sits in front of a huge percentage of the world's websites, they see the hits before almost anyone else. They don't just show pretty lines; they show "Percentage of HTTP traffic mitigated." That’s a real metric. If you see a massive spike in a specific region on Cloudflare Radar, something is actually happening.
Radware is another big name. Their live map focuses on the "prospect" of an attack. They categorize things by industry. This is huge because hackers don't just attack countries; they attack sectors. One week it’s finance. The next, it’s gaming. If you’re a sysadmin for a bank, you don't care about a DDoS attack on a Minecraft server, even if that attack is technically "bigger" in terms of Gigabits per second.
Then there is Spur. Not many hobbyists know about them, but they track the "nodes" of the internet. They look at the infrastructure. Understanding the infrastructure is how you move past the "pew-pew" lasers and into actual threat intelligence.
The 2026 reality: Terabit-scale nightmares
We are past the days when a "big" attack was 10 Gbps. That’s a joke now. In the last few years, we've seen attacks exceeding 3 and 4 Terabits per second (Tbps).
To put that in perspective: that is enough data to download the entire library of Netflix in a few seconds. No single server can survive that. No "firewall" in a box can stop it. This is why the internet ddos attack map looks so frantic. The scale of the "Mirai" botnet or the more recent "Mantis" and "Storm-1133" clusters is staggering.
Hackers are now using "Rapid Reset" techniques (exploiting HTTP/2) to generate millions of requests per second with very little effort. When this happens, the maps light up like a Christmas tree. But often, the map lags. The attack is over in 90 seconds, but the map stays red for ten minutes because of how the data is processed.
Does a map actually help you?
If you’re a regular person? No. It’s just interesting.
If you’re a business owner? Sorta.
Monitoring an internet ddos attack map can give you a heads-up if there is a "weather event" on the internet. If you see the entire East Coast of the US lighting up on multiple maps, and your website is suddenly slow, you know it’s likely not your code. It’s the pipes.
Actionable steps for dealing with the "Red Map" reality
Don't just stare at the glowing lines. If you're worried about the threats these maps visualize, you need a proactive stance.
- Audit your DNS. Most DDoS attacks target the easy stuff first. If your DNS provider doesn't have built-in DDoS protection (like what you get with Cloudflare, AWS Shield, or Akamai), you are a sitting duck.
- Stop trusting "Source" data blindly. When you look at a map and see an attack coming from a specific country, don't go blocking that entire country's IP range. You'll likely just block your own customers. Hackers use proxies.
- Check the "Status" pages. Instead of just a map, bookmark the status pages of major Tier-1 providers like Lumen (formerly CenturyLink), Telia, and NTT. When these guys have a problem, the whole world feels it.
- Understand "Packet Analysis." If you really want to be an expert, learn to read a PCAP file. A map shows you the fire; a PCAP file tells you what kind of fuel the arsonist used.
- Implement Rate Limiting. Most modern web servers (Nginx, Apache) allow you to limit how many requests a single IP can make per second. It’s a basic move that stops low-level "script kiddie" attacks cold.
The internet is a messy, chaotic place. An internet ddos attack map tries to bring order to that chaos by making it visual. Just remember that the map is a representation, not the reality. The real battle happens in the headers, the TTL values, and the scrubbers of massive data centers. Enjoy the light show, but keep your patches up to date and your backups off-site.
The next time you see a massive red line arcing across the Atlantic on your screen, don't panic. Check your own latency. Check your error logs. The map is just the weather report—it's up to you to build the umbrella.
Expert Insight: Most modern DDoS attacks are "multi-vector." This means the attacker is hitting you with three different methods at once (like a SYN flood, a UDP reflection, and an application-layer attack) just to see which one breaks you first. A map will usually only show the loudest one. To stay safe, you have to defend against the quiet ones too.
Next Steps for Implementation:
- Identify your most critical public-facing IP addresses.
- Cross-reference your hosting provider's default DDoS mitigation limits (some only provide up to 1 Gbps of "free" protection).
- Set up automated alerts via a third-party monitoring service like UptimeRobot or Pingdom so you know you're down before the "map" tells you.