You probably think of North Korea as a place where time just... stopped. Most of us imagine gray buildings and 1950s technology, but the reality inside their local area network is a bit weirder. They didn’t just buy a bunch of Windows licenses and call it a day. Instead, they built the North Korea operating system known as Red Star OS. It’s a Linux-based frankenstein of a system that tells us more about the regime’s paranoia than any satellite photo ever could.
It's Linux. But not the kind of Linux you'd use to feel like a "hacker" in a coffee shop.
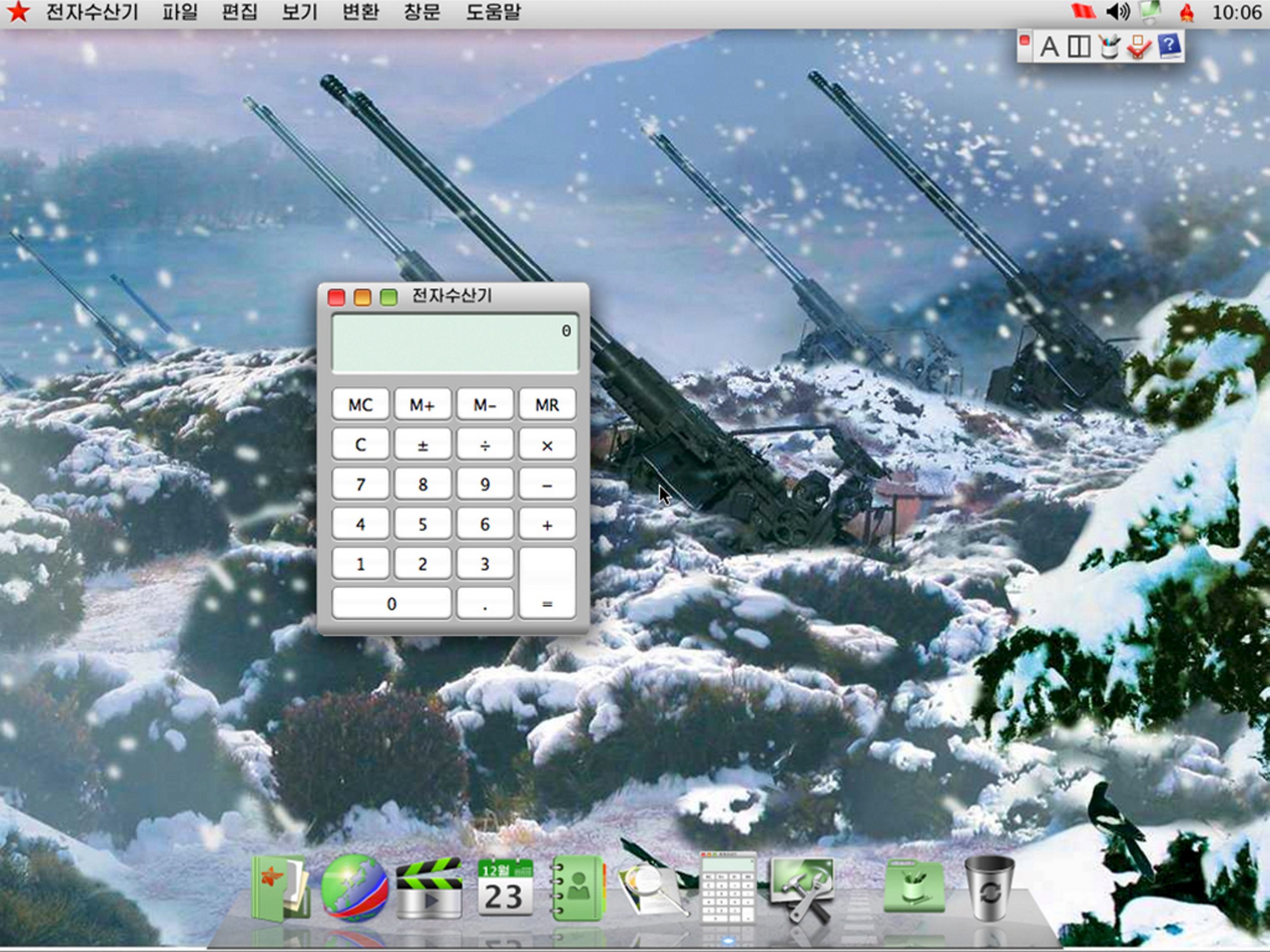
Originally, the DPRK used a localized version of Windows. That changed around 2002. The Korea Computer Center (KCC) in Pyongyang decided they needed their own proprietary software. Why? Because when you’re a hermit kingdom, you don’t trust Microsoft. You don't trust backdoors. You want a digital wall that matches the physical one. Red Star OS is that wall. It’s been through several iterations, moving from a Windows 7 look-alike to something that looks exactly like macOS. Seriously, if you squint, Red Star OS 3.0 is a dead ringer for an older version of OSX.
The Surveillance Engine Under the Hood
The most fascinating (and terrifying) thing about the North Korea operating system isn't the desktop wallpaper or the "Naenara" browser. It’s the watermarking. Researchers Florian Grunow and Niklaus Schiess from the German IT security company ERNW GmbH spent months digging into the code of Red Star OS 3.0. What they found was a sophisticated tracking mechanism.
The OS tags every single file on the computer.
Every. Single. One.
If you plug a USB stick into a computer running Red Star OS, the system takes a unique hardware ID and hashes it into every document, photo, and video on that drive. It doesn't matter if you just want to share a movie or a PDF; the file is permanently "signed." If that file ends up in the wrong hands, the government can trace exactly which computer it came from. This isn't just about catching spies. It’s a direct response to the "grassroots" information trade where North Koreans smuggle in South Korean dramas (K-dramas) and foreign news on thumb drives. The OS turns the computer into a digital snitch.
Why It Looks Like a Mac
It’s a bizarre aesthetic choice. Version 2.0 of Red Star OS looked like Windows 7, likely because that’s what the population was used to seeing. But by version 3.0, the KCC shifted the entire UI to mimic Apple. Rumors suggest this was a direct order from Kim Jong Un, who has been photographed with iMacs and iPads in the past.
But don't let the "pretty" icons fool you.
The system is locked down tighter than a drum. There is a daemon (a background process) called "oppv" that constantly checks if any core system files have been modified. If you try to disable the firewall or the virus scanner—which, ironically, needs constant updates to stay "secure"—the computer will simply reboot. It’s a self-healing system designed to prevent anyone, even a savvy user, from gaining root access or bypassing the state's filters.
The "Naenara" Browser and the Intranet
North Korea doesn't have the Internet. They have the "Kwangmyong." It’s a nationwide intranet. It’s a walled garden that contains maybe a few thousand state-approved websites. The browser used to access this is called Naenara, which is basically a heavily modified version of Mozilla Firefox.
When you use Naenara, you aren't surfing the web. You're browsing a curated list of propaganda, educational materials, and state-run "news" outlets. The browser is hardcoded to only accept certain IP ranges. If you tried to type in "https://www.google.com/search?q=google.com," it simply wouldn't know where to go. The DNS (Domain Name System) is entirely internal.
Technical Specs and Compatibility
You’d think it would be ancient, but Red Star OS is surprisingly competent from a technical standpoint.
- It runs on a Linux kernel (Version 2.6 or 3.x depending on the build).
- The "Sogwang" office suite is a fork of OpenOffice.
- There’s a pre-installed media player and some basic games.
- It uses a "Wine" variant to run some older Windows applications.
The hardware requirements are remarkably low. It was designed to run on the "Arirang" or "Ryonghung" tablets and various locally assembled PCs that use older Intel or domestic components. Because the code is optimized for specific, older hardware, it actually feels quite snappy. It’s efficient. It’s lean. It’s also a total dead end for any developer not working for the KCC.
Is There a Red Star OS 4.0?
Information on version 4.0 is sparse, but it exists. Reports from 2017 and 2018 suggested that a server-side version was being deployed, and a desktop version followed shortly after. While we haven't seen a massive leak of 4.0 like we did with 3.0, it appears the regime is moving toward more cloud-based integration. They want to sync devices. They want the tablet in a citizen's hand to be perfectly mirrored and monitored by the central servers.
The goal of the North Korea operating system isn't to innovate. It’s to isolate.
By creating a unique environment, the DPRK ensures that foreign software (and the ideas that come with it) can't easily take root. It makes the "official" way of doing things the only way. If you want to use a computer in Pyongyang, you play by their rules, on their kernel, with their watermarks watching your every move. It’s a masterclass in digital sovereignty used for the sake of total control.
How to Safely Explore This World
If you're a tech enthusiast, you might be tempted to go find an ISO of Red Star OS and fire it up. You can. It's out there on archive sites. But honestly? Be careful.
- Use a Virtual Machine: Never, ever install this on your actual hardware. Use VirtualBox or VMware.
- No Network Connection: Disable the virtual network adapter before you boot it. You don't want a "phone home" feature reaching out from your IP address.
- Don't Input Personal Data: Treat it like a virus. It’s an interesting artifact, but it’s built by a regime that specializes in cyber warfare.
- Expect Frustration: Unless you speak Korean, navigating the menus is a nightmare, though the macOS-clone icons make it somewhat intuitive.
Moving Forward with Digital Sovereignty
Understanding the North Korea operating system helps us realize that the internet isn't actually "global." It’s fragmented. While the rest of the world debates privacy and data collection by corporations, North Korea has solved the problem by becoming the sole data collector. They've weaponized the Open Source movement to create the ultimate closed system.
To see this in action, you can look into the work of Will Scott, a former teacher at the Pyongyang University of Science and Technology. He was one of the few Westerners to actually use the system in its native environment. His photos and reports provide the most grounded look at how everyday students interact with Red Star.
For those interested in the cybersecurity aspect, checking out the 32C3 (32nd Chaos Communication Congress) presentation "Lifting the Veil on Red Star OS" is essential. It’s the definitive technical teardown of the system's security features. You’ll see exactly how the watermarking works and why the "security" of the OS is actually its biggest vulnerability for the user.
📖 Related: Why a Diagram of Mars Planet Still Confuses Most People
The next step for anyone curious is to research the "Koryolink" network. This is the mobile side of the equation. Just as Red Star OS controls the desktop, a specialized version of Android (often referred to as "North Korean Android") controls the mobile space, complete with the same watermarking and surveillance tools. Studying both gives you a full picture of a society where the code is the law.