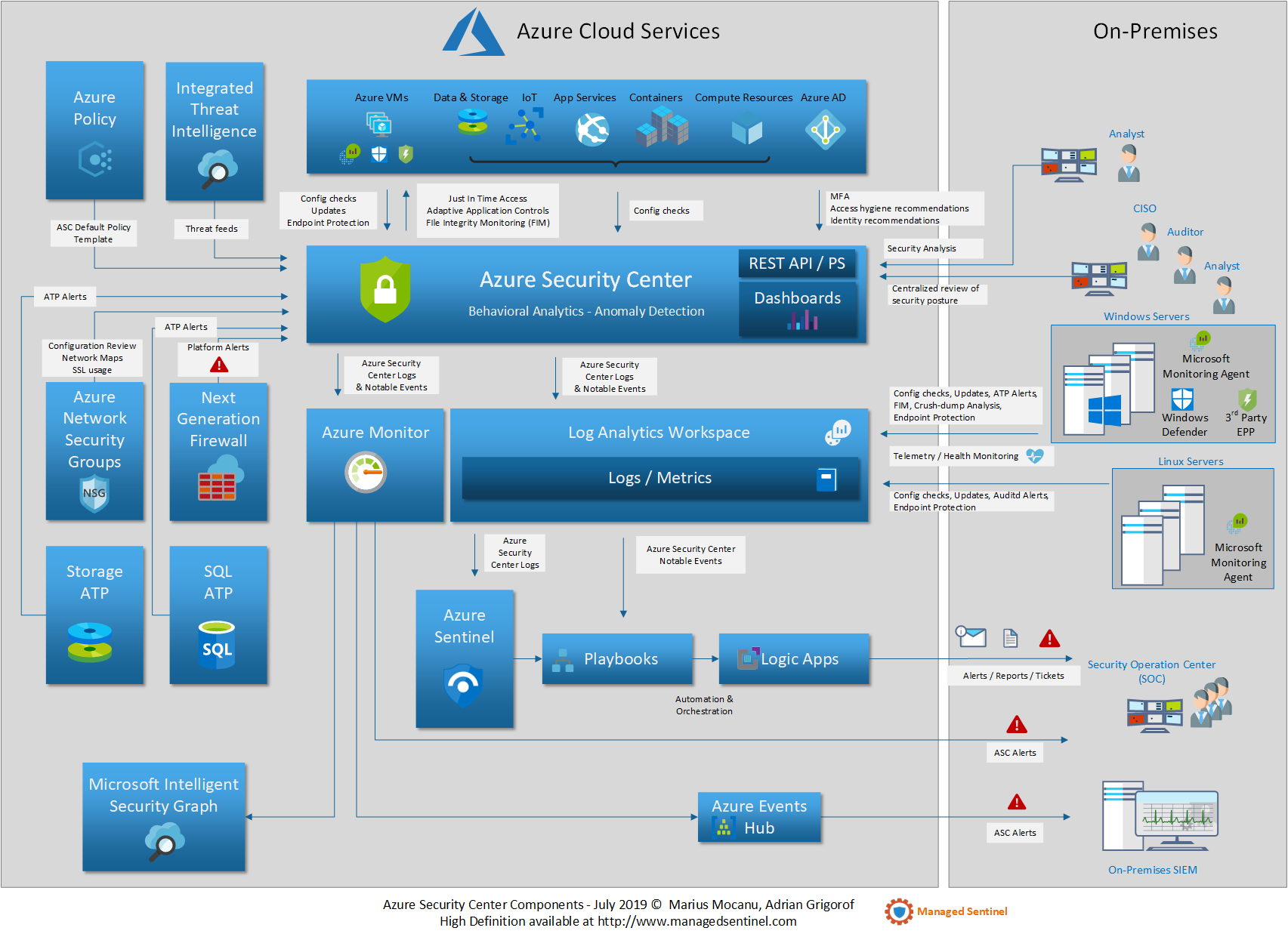
Cloud security is messy. Honestly, if you’ve spent more than five minutes in the Azure portal, you know that things move fast—sometimes too fast for our own good. Names change, features merge, and suddenly the tool you used yesterday has a different icon and a brand-new acronym. That’s exactly what happened with security center in azure.
Technically, it doesn't exist anymore. Not by that name, anyway.
Microsoft rebranded Azure Security Center and Azure Defender into a single, unified platform called Microsoft Defender for Cloud back in late 2021. But here’s the thing: most of us still search for the old name. Why? Because the core mission hasn't changed. You’re still trying to figure out why that one storage account is publicly accessible or why your virtual machines aren't patched. You’re looking for a dashboard that tells you, in plain English, how likely you are to get hacked today.
The Identity Crisis of Security Center in Azure
When Microsoft shifted everything under the "Defender" umbrella, they weren't just being difficult. They were trying to solve a sprawl problem. Back in the day, the security center in azure was purely about your Azure resources. But we don't live in an Azure-only world anymore. Most companies are running stuff on AWS, Google Cloud, and on-premises servers.
If you go looking for the old security center today, you’ll find a beast that manages security posture (CSPM) and workload protection (CWPP) across every cloud you own. It’s ambitious. It’s also kinda overwhelming.
The platform is essentially split into two halves now. First, you’ve got the free stuff. This is the basic posture management. It gives you that famous "Secure Score"—a number that usually starts out depressingly low and makes you feel like you’ve failed at your job. Then, there’s the paid stuff. This is where "Defender for Servers" or "Defender for SQL" comes in. This is the proactive, "hey, someone is trying to brute-force your password right now" side of the house.
Why Your Secure Score is Probably Liars’ Gold
Let’s talk about that Secure Score. It’s the first thing you see when you open the console. It looks like a simple metric. 0% is bad, 100% is perfect. Easy, right?
Not really.
I’ve seen environments with a 90% Secure Score that were actually less secure than ones with a 40% score. How? Because the score only measures what it can see. If you have a massive, unmanaged legacy database sitting on a VM that isn't being monitored, it won't hurt your score. But it will definitely get you fired when it leaks.
The security center in azure—or Defender for Cloud—is a tool, not a strategy. You have to treat the recommendations with a bit of skepticism. Sometimes, the "fix" the tool suggests will break your entire application. For instance, it might tell you to enforce "MFA for all users." Sounds great. Until you realize that includes your service accounts used for automated deployments, and suddenly your whole CI/CD pipeline grinds to a halt because a bot can't check its phone for a code.
Real-World Messiness: Multi-Cloud and The "Single Pane of Glass" Myth
We’ve been promised a "single pane of glass" for a decade. It’s the holy grail of IT. Microsoft claims that by evolving the security center in azure into a multi-cloud tool, they’ve finally done it.
They’ve come close. You can actually connect an AWS account to your Azure portal now. It uses the AWS API to pull in metadata and check it against industry standards like CIS or PCI DSS. It’s cool. It’s also weirdly surreal to be looking at your Amazon S3 buckets inside a Microsoft dashboard.
But here is the reality: the integration isn't perfect.
If you’re managing AWS through Azure, you’re going to run into latency. You’re going to find that some AWS-specific nuances get lost in translation. It’s better than nothing, but don't expect it to replace a dedicated AWS security expert. It’s a bird’s eye view, not a microscope.
The Features That Actually Matter (And The Ones That Don't)
Forget the marketing fluff. If you're digging into the security center in azure today, there are three things you should actually care about.
Just-in-Time (JIT) VM Access. This is a lifesaver. Usually, people leave RDP or SSH ports open to the world because they’re "testing" something. Three weeks later, they’re still open. JIT closes those ports by default. When you need in, you request access, the portal opens the port for your specific IP address for a few hours, and then slams it shut again. It’s simple. It works.
Regulatory Compliance Dashboards. If your boss comes to you asking if you’re "SOC 2 compliant," you can go into the dashboard, click a button, and get a list of everything you’re failing. It doesn't make you compliant—you still have to do the work—but it gives you the map.
Adaptive Network Hardening. This one is underrated. The platform looks at your actual traffic patterns. If it sees that your web server only ever talks to one specific database, it suggests a firewall rule to block everything else. It’s machine learning that actually does something useful instead of just being a buzzword.
What doesn't matter? The "security alerts" for low-priority events. You will get buried in noise. If you try to investigate every "Suspicious SVCHOST process" alert, you will never sleep. You have to tune the engine.
The Cost: Where Azure Gets Their Pound of Flesh
Azure isn't a charity. While the basic "Secure Score" and recommendations are free, the real protection—the stuff that used to be called Azure Defender—is expensive.
💡 You might also like: Black and Blue Streaming Explained: Why Your Screen Looks Weird and How to Fix It
It’s usually billed per resource per hour. If you have 500 virtual machines and you turn on Defender for Servers, your bill is going to jump. Fast.
Many teams make the mistake of turning everything on at once. Don't do that. Start with your most critical "Crown Jewel" assets. Protect your production SQL databases and your public-facing web apps first. You can probably afford to leave that dev/test sandbox on the free tier for a while.
Moving Beyond the Dashboard
Look, at the end of the day, the security center in azure is just a reporter. It tells you that your house is on fire. It doesn't always put the fire out for you.
I’ve met plenty of admins who spend all day clearing alerts in the portal but never actually fix the underlying infrastructure code. That’s a hamster wheel. If the portal tells you that your disks aren't encrypted, don't just click the "Fix" button. Go back to your Terraform or Bicep templates and change the code. If you fix it in the portal manually, the next time you deploy your infrastructure, it’ll just be broken again.
The true power of Microsoft’s security evolution is the API. You can export all these recommendations into Power BI or send them to a Sentinel workspace (Microsoft’s SIEM). That’s where the big kids play. When you start automating the response to these alerts—like automatically isolating a VM if it shows signs of ransomware—that’s when you’ve actually moved the needle.
Practical Next Steps for Your Environment
If you’re staring at a screen full of red icons and a Secure Score of 12%, don't panic. You can’t fix a cloud environment in a day.
First, turn on MFA for everyone. Honestly. If you do nothing else, do this. It’s the single biggest jump you’ll get in your score and your actual safety.
Second, filter by "Quick Fix." In the recommendations list, there’s a little lightning bolt icon. These are things Microsoft can automate for you. It’s the low-hanging fruit. Spend an hour clicking those buttons just to get some momentum.
Third, set up Email Notifications. No one logs into the Azure portal every morning to check for alerts unless they’re forced to. Set up a notification so that if a "High" severity alert triggers, your security team gets an email or a Slack ping immediately.
Lastly, audit your subscriptions. The security center in azure can only protect what it can see. If you have "Shadow IT"—devs spinning up subscriptions on their own credit cards—you’re blind. Use Azure Blueprints or Policies to force new subscriptions into your management group so they automatically inherit your security settings.
The cloud is inherently insecure by default because it’s built for convenience. It’s your job to turn the knobs and tighten the screws. The tools are all there; you just have to stop looking at the dashboard and start doing the work.