Ever tried to drag a simple PDF from your desktop into a shared office folder only to see that mocking "Access Denied" popup? It’s infuriating. You know the file is yours. You know the network exists. Yet, the file manager right networks setup—that invisible web of permissions governing who can see, move, or delete data—has decided you aren't worthy. Honestly, most people think network file management is just about having a fast Wi-Fi connection or a chunky server in the basement. It’s not. It’s actually a complex, often messy tug-of-war between security protocols and user convenience that most IT departments are still struggling to balance.
Networked file management is basically the circulatory system of a modern business. If the "rights" or permissions are too tight, the business chokes because nobody can collaborate. If they're too loose, you're basically leaving your front door wide open for ransomware.
The Messy Reality of File Manager Right Networks
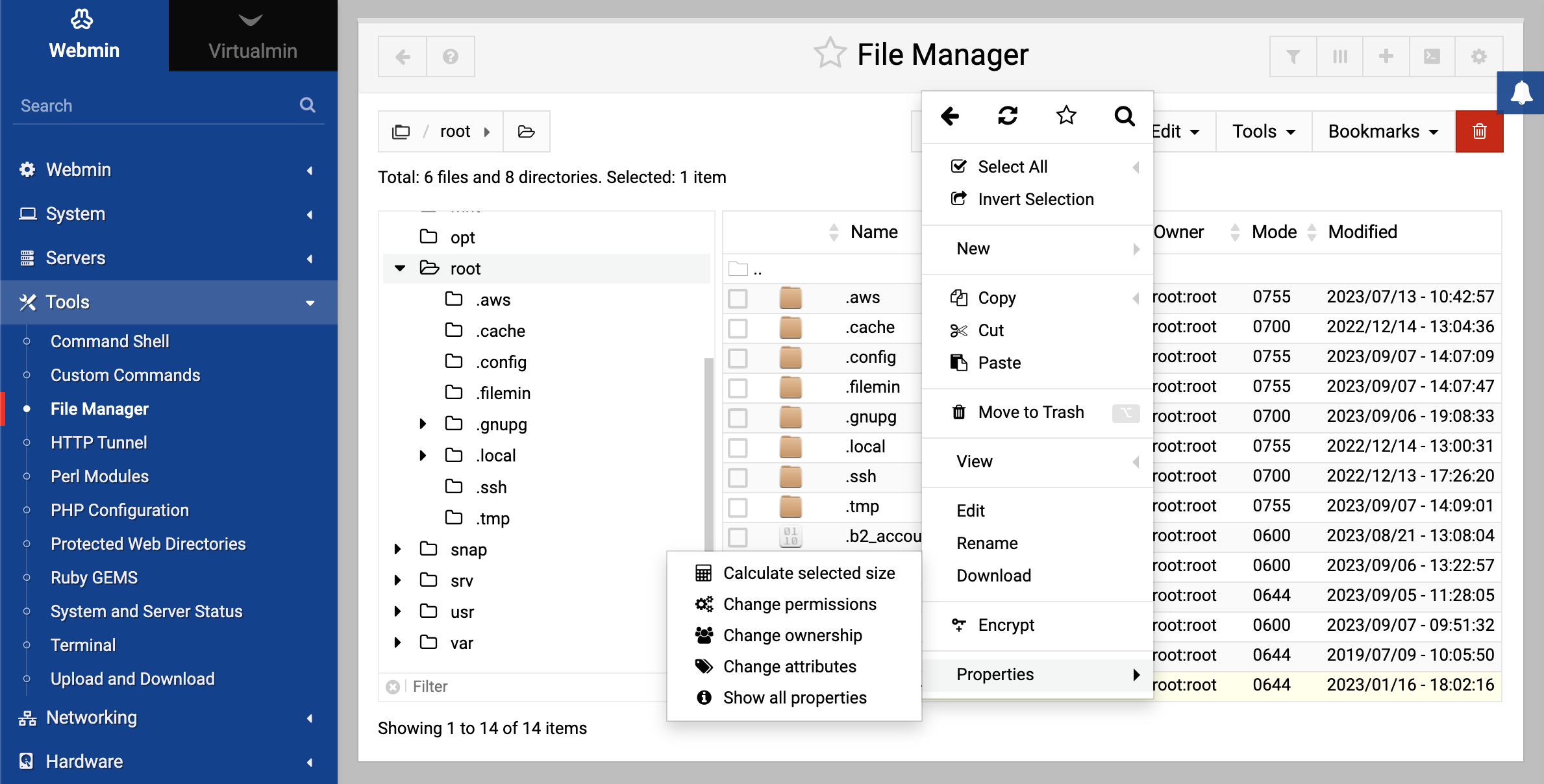
When we talk about file manager right networks, we’re diving into the world of Access Control Lists (ACLs) and protocols like SMB (Server Message Block) or NFS (Network File System). For the average person using Windows File Explorer or macOS Finder, these are just background noise. But the moment you connect to a NAS (Network Attached Storage) or a corporate SAN, these protocols start dictate your life.
Permissions aren't just "on" or "off." They’re layered. You have "Read," "Write," "Modify," and the big boss: "Full Control." Most experts, like those at Microsoft or the SANS Institute, suggest a "Least Privilege" model. This means you give someone the absolute bare minimum access they need to do their job. Sounds smart, right? In practice, it’s a nightmare. Marketing needs to see the Sales folder for one specific project, but the file manager right networks logic says "No." So, what happens? People start using Dropbox or personal Google Drives to bypass the network. Now you have "Shadow IT," and your data is everywhere it shouldn't be.
Why Your Permissions Probably Suck
The biggest mistake is thinking that permissions are a "set it and forget it" task. They aren't. Networks grow. People quit. Roles change.
Inheritance is usually where things go sideways. In a standard file manager setup, a sub-folder "inherits" the rights of the folder above it. If you accidentally give the "Everyone" group access to the "Company" folder, every single sub-folder—including Payroll and HR—is suddenly a free-for-all. It happens more than you’d think. Even at massive firms. I’ve seen cases where interns had access to executive salary spreadsheets simply because a nested folder didn't have inheritance blocked properly.
Then there’s the issue of "Nested Groups." This is when you put a group inside another group. It makes sense for organization, but it creates a "Permissions Soup" that is nearly impossible to audit. Tools like Netwrix or Varonis exist specifically because humans are terrible at keeping track of these sprawling file manager right networks. They scan your system and show you that, somehow, a former employee from 2018 still has "Modify" rights to your active client list.
Protocols Matter More Than You Think
If you're using a Mac and trying to talk to a Windows server via SMB, you've probably noticed it feels... sluggish. Or files just disappear. That’s because SMB (created by IBM and polished by Microsoft) and Apple’s implementation don’t always play nice.
- SMB 3.1.1: This is the modern standard. It’s fast and encrypted. If your network is still running SMB 1.0, stop. It’s a massive security hole that led to the global WannaCry outbreak.
- NFS: Mostly used in Linux environments. It’s incredibly fast but lacks the granular "User-friendly" permission interface of Windows.
- SFTP: It’s old school, but for remote file management, it’s still a king for security.
The Cloud Complication
Everything is moving to OneDrive, SharePoint, or Box. You’d think this would make file manager right networks easier. Nope. It just adds a new layer of abstraction. Now you aren't just managing NTFS permissions; you're managing "Sharing Links."
Anyone who has ever tried to manage a large SharePoint library knows the pain of "Unique Permissions." The moment you stop inheriting from the site level and start giving specific people access to specific files, the sync engine starts to chug. Microsoft actually warns against having too many unique permissions because it literally slows down the database. You end up with a network that is technically functional but practically unusable.
Auditing: The Only Way to Stay Sane
You cannot manage what you can’t see. A truly professional file manager right networks strategy requires regular audits. This isn't just about security; it's about cleanup. Ghost folders, "New Folder (2)," and data that hasn't been touched since the Bush administration are clogging up your expensive NVMe storage.
Experts like Dr. Eric Cole often emphasize that "prevention is ideal, but detection is a must." If someone starts changing rights on a sensitive directory, your system should scream. File Integrity Monitoring (FIM) is the pro-level version of this. It tracks every "Right" change in real-time. If an admin account suddenly grants "Full Control" to a guest account at 3:00 AM, the system shuts it down.
👉 See also: Audi e-tron SUV: Why It Still Matters in 2026
Actionable Steps for Better Network Control
Stop treating your file manager like a junk drawer. If you want a network that actually works without compromising security, you need a proactive stance.
Standardize your naming conventions. This sounds boring, but if folders are named clearly, admins are less likely to make mistakes when assigning rights. "Project_Alpha_Internal" is much clearer than "AlphaStuff."
Kill SMB 1.0. Seriously. Check your server settings right now. If it's enabled, you are inviting disaster. Modern file manager right networks should exclusively use SMB 3.0 or higher for the sake of encryption and "dialling home" to the domain controller securely.
Enforce a "No Individual Permissions" rule. Never, ever assign a right to a single person (e.g., "John Smith has Read access"). Always assign rights to a Group (e.g., "Accounting_Read"), and then put John Smith in that group. When John leaves, you just disable his account, and the group remains intact. It’s cleaner. It’s faster. It’s less likely to break.
Use "Access-Based Enumeration." This is a killer feature in Windows Server. If a user doesn't have "Read" rights to a folder, they shouldn't even see it. It just vanishes from their view. This prevents "Curiosity Clicking" where users try to get into folders they know they shouldn't be in.
✨ Don't miss: Why the Apple Store Upper West Side Still Hits Different
Implement a Data Retention Policy. Not all data needs to live on your primary network. Move old files to "Cold Storage" (like Amazon S3 Glacier or an offline NAS). This reduces the "Attack Surface" of your file manager right networks because there's less data for a hacker to encrypt or steal.
The goal isn't to build a digital fortress that no one can enter. The goal is to build a system where the right people have the right access at the right time, without having to call IT every five minutes. It takes work, but it beats losing your entire database to a permission slip-up.
Next Steps for Implementation:
- Map your existing Shares: Use a tool like "AccessEnum" (it’s free from Sysinternals) to see exactly who has access to what right now. You’ll be surprised at what you find.
- Consolidate Groups: Look for redundant Active Directory groups. If you have "Sales" and "Sales_Team" and "Sales_Staff," pick one and merge.
- Test SMB Signing: Ensure SMB signing is required on your network to prevent man-in-the-middle attacks, which can intercept file transfers and modify rights on the fly.