Steven Levy wrote a book in 1984 that basically changed how we look at the guys in the basement. It’s called Hackers: Heroes of the Computer Revolution. If you haven't read it, you’ve probably still felt its ripples. It isn't just a history book. It’s a manifesto for a world that didn't exist yet.
Before this book, "hacker" wasn't a dirty word. It didn't mean someone stealing your credit card info or shutting down a hospital's server for ransom. It meant someone who stayed up until 4:00 AM fueled by bad coffee and a desperate need to make a machine do something the manual said it couldn't.
Levy tracked three generations of these people. He started with the model train nerds at MIT in the 50s and 60s. Then he moved to the hardware hackers building the Altair and the Apple I in the 70s. Finally, he hit the game programmers of the early 80s.
It’s a wild ride.
What Most People Get Wrong About the Hacker Ethic
People hear "Hacker Ethic" and they think it’s about breaking rules for the sake of it. Not really. At its core, the philosophy Levy outlined was about the Hands-On Imperative.
Basically, if you can fix something or improve it, you should have the right to do so. Access to computers should be unlimited and total. Information wants to be free.
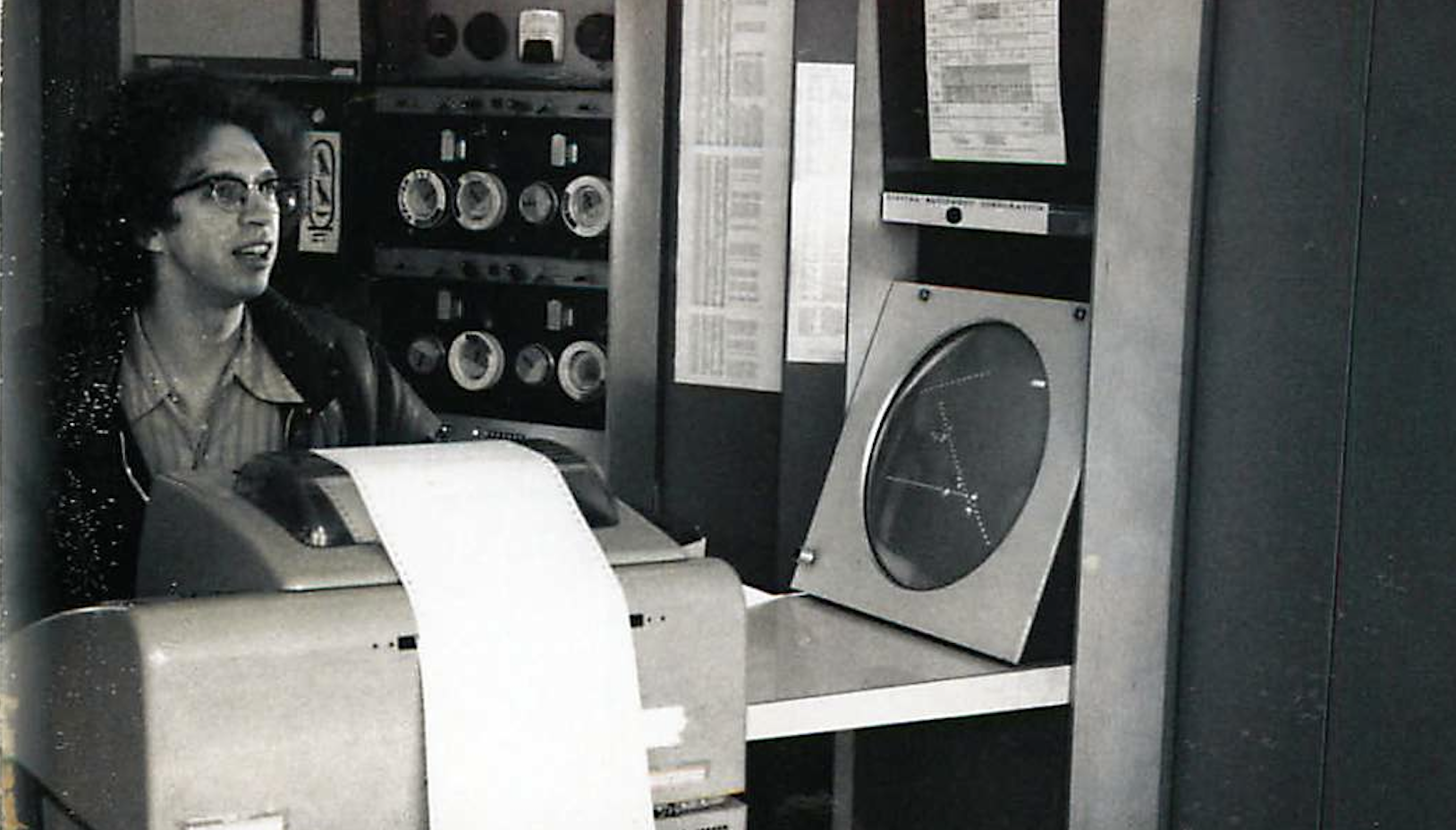
The Tech Model Railroad Club (TMRC) at MIT is where the term really gained its modern legs. These guys weren't trying to take down the government. They were trying to make the signals on their massive model train layout work more efficiently. They treated the computer—specifically the TX-0 and later the PDP-1—as the ultimate toy.
They hated "The Priesthood."
That’s what they called the guys in white lab coats who guarded the mainframes. Back then, you didn't just walk up to a computer. You submitted a stack of punch cards and waited 24 hours for a printout that usually just said "Error." The hackers at MIT thought that was garbage. They wanted to touch the machine. They wanted to live inside the logic.
👉 See also: The Facebook User Privacy Settlement Official Site: What’s Actually Happening with Your Payout
This mindset gave us the first video games, like Spacewar!. It wasn't a product. It was a gift. Nobody charged for it. They just passed the paper tape around. This is the part of Hackers: Heroes of the Computer Revolution that feels most alien today in our world of subscriptions and locked-down hardware.
The Homebrew Era: When Hackers Built the Future in Garages
The second "generation" in the book is where things get messy and iconic. This is the 1970s. The Homebrew Computer Club. Northern California.
Lee Felsenstein. Fred Moore. Steve Wozniak.
These guys were the bridge. They took the academic brilliance of MIT and brought it to the hobbyist level. They were anti-war, pro-community, and deeply suspicious of big corporations like IBM.
Wozniak is the standout here. In Hackers: Heroes of the Computer Revolution, Levy describes Woz as the "ultimate hacker." He didn't care about the money. He just wanted to show off his clever engineering to his friends at the club. When Steve Jobs saw the Apple I, he saw a business. Woz just saw a really cool circuit board.
The Conflict of Commercialization
This is where the "Hero" part of the title starts to get complicated.
As soon as computers became products, the Hacker Ethic hit a wall. Bill Gates wrote his famous "Open Letter to Hobbyists" in 1976. He basically told the Homebrew guys to stop stealing his software. He argued that if they didn't pay for Altair BASIC, he couldn't afford to make more.
The hackers were offended.
✨ Don't miss: Smart TV TCL 55: What Most People Get Wrong
To them, software was like a joke or a recipe. You share it. You improve it. You don't lock it behind a price tag. This tension between "Information wants to be free" and "Developers need to eat" is the central drama of the middle of the book. It’s a debate we’re still having today with open-source software versus proprietary AI models.
The Third Generation: Sierra On-Line and the End of Innocence
The final section of the book covers the early 80s. This is the era of the "Game Hackers."
Ken and Roberta Williams. On-Line Systems (later Sierra On-Line).
These people were different. They weren't building the machines; they were building worlds inside them. Mystery House. King's Quest. They were making millions of dollars.
Levy paints a somewhat tragic picture here. You see the transition from guys sleeping under their desks because they love the code, to guys sleeping under their desks because they have a shipping deadline for a Christmas release.
The "Hero" status was shifting. The hacker was becoming a rockstar, but with that came the corporate machine. Marketing departments. Lawyers. Copy protection.
Copy protection was the ultimate insult to the Hacker Ethic. It was a literal lock on the information. Hackers spent their nights breaking those locks just to prove they could, starting a cat-and-mouse game that has lasted for forty years.
Why This History Matters in 2026
You might wonder why a book from 1984 is still relevant. Honestly, it’s because the "Hacker Ethic" is the DNA of everything you use.
🔗 Read more: Savannah Weather Radar: What Most People Get Wrong
- Linux exists because of this book's philosophy.
- Wikipedia is the Hacker Ethic applied to general knowledge.
- The Right to Repair movement is just the "Hands-On Imperative" with a new name.
We live in an age where our devices are "black boxes." You aren't supposed to open your iPhone. You can't see the code running your social media feed. The hackers Levy wrote about would have hated this. They believed you should be able to "peek and poke" at every bit of data.
When you read Hackers: Heroes of the Computer Revolution, you realize that the "revolution" wasn't about the hardware. It was about the power dynamic between the user and the creator.
Key Lessons from the Hacker Ethic
- Bureaucracy is a bug. Hackers bypass systems to get work done. If a rule stops progress, the rule is broken, not the person.
- Judging should be based on hacking, not criteria. They didn't care if you were 12 years old or didn't have a degree. Can you code? That was the only question.
- You can create art and beauty on a computer. This was a radical idea in 1960. Now, it's our entire culture.
The Complicated Legacy of the Word "Hacker"
It’s kind of a bummer how the word evolved.
By the late 80s and 90s, the media turned "hacker" into "cyber-criminal." The nuance was lost. Levy actually added an afterword in later editions to address this. He differentiates between the "crackers" (who break things) and the "hackers" (who build things).
But the label stuck.
Today, if you tell your grandma you're a hacker, she’ll probably check her bank account. If you tell a recruiter at a startup, they might give you a signing bonus. We’re in this weird middle ground where the spirit of the MIT basement is celebrated in "hackathons," but the actual practice of unauthorized exploration is more legally dangerous than ever.
Actionable Insights: How to Use the Hacker Ethic Today
You don't need to be a C++ wizard to adopt the mindset from Hackers: Heroes of the Computer Revolution. It’s more of a psychological framework.
- Adopt the "Hands-On Imperative": Stop treating your tools like magic. Whether it's a spreadsheet or a piece of furniture, try to understand how it works. Take it apart (metaphorically or literally).
- Value Merit Over Pedigree: In your own projects or business, look for people who "do" rather than people who "have." The best contributors often come from outside the traditional system.
- Share Your "Paper Tapes": If you find a better way to do something, share it. Open-source your workflow. The more information flows, the better the entire system becomes.
- Resist the Priesthood: Don't let "experts" gatekeep your curiosity. If you want to learn how something works, the resources are out there. The hackers of the 60s had to steal computer time at night; you have a supercomputer in your pocket.
The computer revolution isn't over. It just changed forms. We are currently in the middle of a new one with AI and decentralized tech. The question is whether we will follow the Hacker Ethic—keeping things open, transparent, and decentralized—or if we will let the new "Priesthood" take the keys.
Reading Levy’s work is a reminder that the best parts of our digital world weren't built by corporations. They were built by people who were just too curious to follow the rules.
Next Steps for the Curious:
- Find a copy of the 25th Anniversary Edition of the book; the updates are worth it.
- Look up the "Jargon File" online to see the actual language these original hackers used.
- Check out the documentary Revolution OS if you want to see how these ideas birthed the open-source movement.