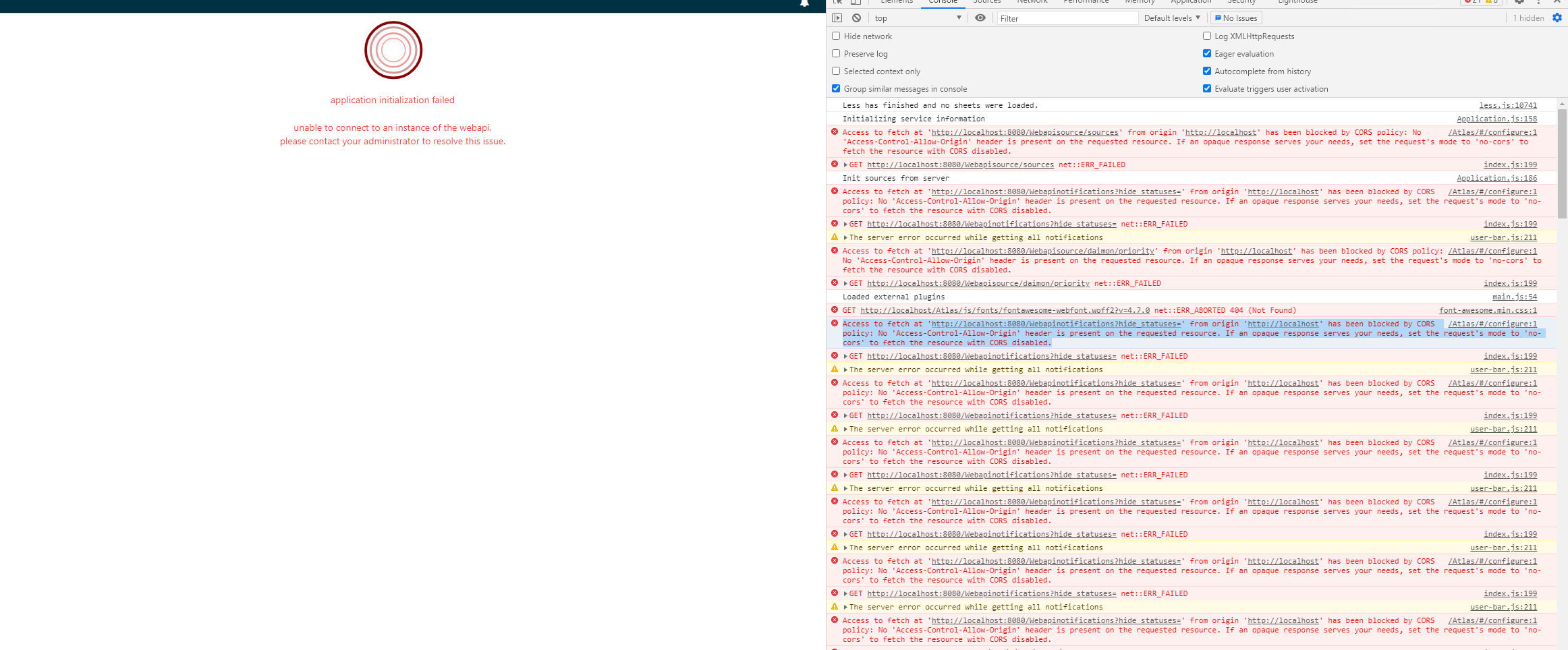
You've been there. You're deep into a coding session, the logic is finally clicking, and you make that one crucial fetch request to an external API. Then, the console turns red. A wall of text screams about "Cross-Origin Request Blocked." It's frustrating. It feels like a personal insult from the browser. Honestly, learning how to bypass CORS error is basically a rite of passage for every web developer on the planet.
CORS isn't a bug. It's actually a security feature. It stands for Cross-Origin Resource Sharing. It exists because browsers don't trust anybody by default. If you’re on site-a.com, the browser assumes you shouldn't be grabbing private data from site-b.com unless site-b.com explicitly says it's cool. Without it, a malicious site could theoretically script a request to your bank's website and steal your session data. But when you're just trying to get weather data or a list of Pokémon, it feels like a massive roadblock.
The Brutal Reality of the Same-Origin Policy
Everything starts with the Same-Origin Policy (SOP). This is the bedrock of web security. An "origin" is the combination of the protocol (http vs https), the domain, and the port. If any of those three things are different, you're in cross-origin territory.
Try to imagine a world without SOP. You visit a sketchy movie streaming site. In the background, that site runs a script that sends a request to gmail.com. Since you're already logged into Gmail in another tab, the browser sends your cookies along with the request. Boom. The sketchy site now has your emails. This is why browsers are so incredibly strict. CORS is the mechanism that allows us to poke a controlled hole in that wall. It's the "exception" to the rule.
How to Bypass CORS Error During Local Development
When you're just trying to get your frontend to talk to your backend on localhost, you don't want to deal with complex server configurations. You just want the data.
One of the most common ways developers "cheat" during development is using a browser extension. Extensions like "Allow CORS: Access-Control-Allow-Origin" basically intercept the browser's checks and inject the headers you need. It works. It's fast. But it's also a trap. If you rely on an extension, your app will break the second you deploy it to a real server. It's a temporary band-aid, not a solution.
Using a Proxy: The Cleanest Workaround
If you're using a framework like React, Vue, or Angular, you have a better tool: the dev-server proxy. In a package.json file for a Create React App project, you can literally just add a "proxy" field.
"proxy": "http://localhost:5000"
What does this actually do? It tricks the browser. When your frontend asks for /api/data, the dev server intercepts that request and forwards it to your backend. Since the request is happening server-to-server, the browser's CORS rules don't apply. The browser thinks it's talking to the same origin it came from. It's seamless. It's clever. Most importantly, it keeps your code clean.
The Server-Side Fix (The Only Real Way)
Look, if you own the API you're trying to call, you shouldn't be trying to "bypass" anything. You should be fixing the headers. This is the "grown-up" way to handle things.
The server needs to send a specific header back to the browser: Access-Control-Allow-Origin.
If you set this to *, you're telling the browser "I don't care who asks, give them the data." This is fine for public APIs. It's a disaster for private ones. If you're building something secure, you should explicitly list the allowed domains.
Preflight Requests and the OPTIONS Method
Ever noticed a random "OPTIONS" request in your Network tab before your actual "GET" or "POST"? That’s a preflight request.
The browser is essentially asking the server, "Hey, I'm about to send a DELETE request with a custom header. Is that okay with you?" If the server doesn't respond to that OPTIONS request with the right headers, the browser cancels the main request before it even starts. This is a common point of failure. You might have your GET requests configured perfectly, but if your server isn't handled to "speak OPTIONS," you're still going to see that red error message.
When You Don't Own the API
This is the hardest scenario. You're trying to fetch data from a third-party service that doesn't have CORS enabled. You can't change their server. You can't force them to add headers.
You have two choices.
First, you can use a CORS proxy. There are public ones like cors-anywhere. You basically prepend their URL to your API request. The proxy fetches the data for you and adds the necessary headers so your browser doesn't complain.
But there is a catch. Public proxies are slow. They often go down. They can see all the data you're sending through them. Don't ever send passwords or API keys through a public CORS proxy. It's a massive security risk.
Build Your Own Micro-Proxy
The better move? Spend ten minutes writing a tiny Node.js or Python backend.
Use a library like express and cors in Node. Your frontend calls your own backend. Your backend calls the third-party API. Since servers talking to servers don't care about CORS, the request goes through perfectly. Your backend then sends the data back to your frontend with the correct headers.
const express = require('express');
const cors = require('cors');
const axios = require('axios');
const app = express();
app.use(cors()); // This enables CORS for your frontend
app.get('/fetch-data', async (req, res) => {
const response = await axios.get('https://third-party-api.com/data');
res.json(response.data);
});
app.listen(3000);
This is robust. It's secure. It gives you total control. If the third-party API changes their structure, you fix it in one place on your server instead of hunting through your frontend code.
JSONP: The Ancient Relic
You might see mentions of JSONP (JSON with Padding) in old StackOverflow threads. It was a clever hack that exploited the fact that <script> tags aren't subject to CORS. You could load a script from another domain, and that script would wrap the data in a function call.
It worked. But it's dead. Modern APIs don't support it, and it's a security nightmare because you're essentially executing arbitrary code from another domain. If you see someone suggesting JSONP in 2026, politely ignore them. We have better ways now.
Common Misconceptions About CORS
A lot of people think CORS is about preventing the server from processing the request. That's wrong.
In many cases, the server actually performs the action. If you send a POST request that triggers a database change, the server might execute that change, send back a 200 OK, and then the browser blocks the response. The "error" happens in the browser, not the server. This is why CORS is not a substitute for proper server-side authentication and authorization.
Another myth is that curl or Postman tests prove CORS is working. They don't. Postman isn't a browser. It doesn't enforce the Same-Origin Policy. If your request works in Postman but fails in Chrome, that's the classic symptom of a CORS configuration issue.
Specific Implementation Tricks
If you are using Express.js, the cors middleware is your best friend. But don't just use app.use(cors()). Be specific.
- Origin: Only allow your production URL.
- Methods: Only allow GET and POST if that's all you need.
- Allowed Headers: If you use custom headers like
X-Auth-Token, you must explicitly list them. - Credentials: If you need to send cookies (like with
withCredentials: truein fetch), you must setAccess-Control-Allow-Credentialstotrueand you cannot use*for the origin.
In NGINX, you handle this at the configuration level. It's often faster than doing it in the application code. You'd add add_header 'Access-Control-Allow-Origin' 'https://yourdomain.com' always; inside your location block. The always keyword is vital—without it, NGINX might only send the header for successful 200 responses, leaving you in the dark when an error occurs.
Actionable Next Steps
If you are currently staring at a CORS error, here is exactly what you should do:
- Check the Network Tab: Look at the headers of the failed request. Is the
Access-Control-Allow-Originheader missing, or is it just mismatched? - Verify the Port: Remember that
http://localhost:3000andhttp://localhost:3001are different origins. - Inspect the Preflight: If it's a "complex" request (anything other than simple GET/POST/HEAD), make sure your server is handling the OPTIONS request properly.
- Local Dev Hack: If you're in a hurry and it's just local work, use a proxy in your frontend dev server.
- Long-term Fix: Build a server-side proxy or update your API headers to explicitly allow your frontend's domain.
Bypassing CORS isn't about breaking the web. It's about understanding the handshake between the browser and the server. Once you get the hang of the headers, the red text in the console stops being scary. It's just another configuration detail to check off your list.
✨ Don't miss: Getting the Most Out of Apple Store Bridgeport Village: What Locals Actually Need to Know
Stop fighting the browser and start talking to it in its own language. Fix the headers, secure your origins, and get back to building what actually matters._